We were in a pound shop once that was selling marble runs for a pound each. We picked up three boxes, and they've sat around for ages, until this evening when we had a play.
Two sets combined:

Three sets combined:

But it looked too wobbly, so we tried again:

If they still do them, we want to go back and spend twenty pounds and get enough to make a marble run that fills the room...
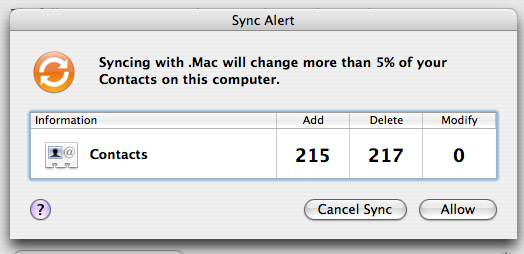
.Mac is a suite of online tools Apple sells to go with their Mac computers. I use the thing purely because it lets my desktop and my laptop both synch various useful bits of data - bookmarks, mail accounts, stored passwords, address book entries, and my calendar.
However, sometimes the synch messes up, as the picture above suggests. When I confirmed the above change, my address book was reduced to a few contacts, plus pages of ones called "No Name" that had no details in them.
Luckily, I had a backup...
In a previous post, I discussed the analysis of an initially robust-looking combination of S-boxes, then suggested two potential extensions of the algorithm to examine.
Read more »
Today, we went down to Bristol to visit Costco and stock up on baby supplies, and to have an outing in the city centre itself.
It was a lovely place to explore, but I was a bit sad - I remember visiting there about 15 years ago and there being a road with loads of big academic bookshops on near the University; but when we went there today, there was just a single small Blackwells. The others had been replaced with clothes shops, shoe shops, and hairdressers, it seemed.
Still, at the end of the day, we headed back up the M5 with Jean asleep. As we approached junction 11A, I commented that we were nearly home - it was just about ten minutes from there. We took the junction, went along the A417 one junction to the A46, but at Crosshands Roundabout - the exit to continue up the A46 was coned off. "ROAD CLOSED - ACCIDENT".
Read more »
Cryptanalysis is the science/art of analysing an encryption system's design to try and figure out how you'd break it.
If encryption systems were used properly, this would be very hard. After all, in that case, all you'd ever have access to was the design of the encryption system and a stream of intercepted encrypted messages.
However, in practice, it's possible to guess parts of the messages (perhaps most start with "Dear ..."), or even to occasionally steal a decrypted message and pair it up with its encrypted version, then study the relationships between them (known plaintext attacks). Or sneak a spy into the organisation being studied, and just ask them to send emails to the person at the other end of the encrypted link, in the middle of the night, at agreed times, so it's easy to spot the encrypted version of the message. Then you have a chosen plaintext attack, which is the most powerful kind.
Read more »




